Introduction
The MITRE framework is used in cybersecurity. It is standard when defining weakness enumerations, vulnerabilities, and attacks. Using this framework allows cyber security professionals to use common terms to describe what they face on a day to day basis. This blog will dive into all the terms and how they are related.
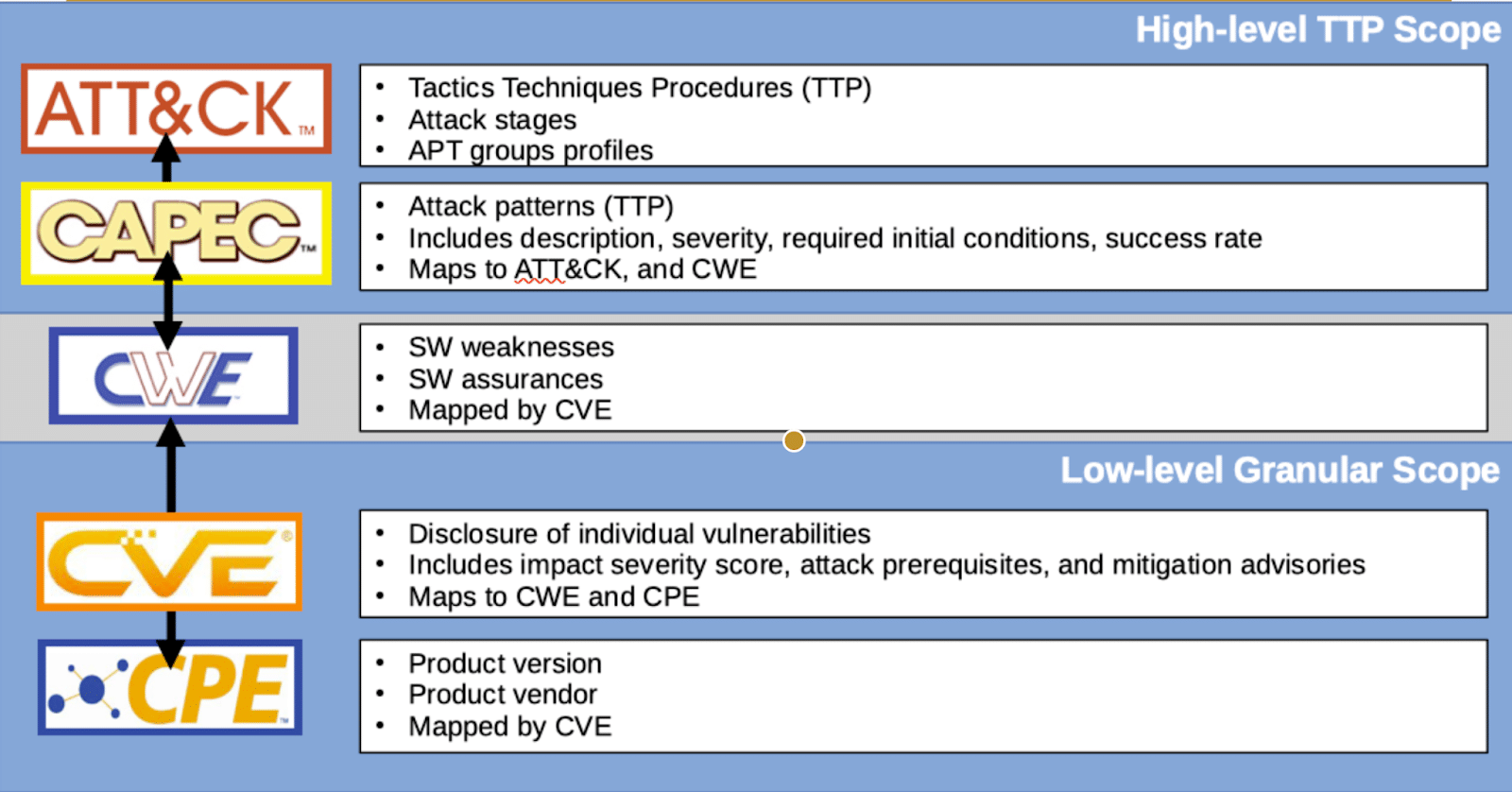
Relationships
Based on the image above it sums up how all of these terms connect. From the CPE, you have CVE that define the vulnerability. From the CVE, you have a CWE which means a common weakness category. From this we get a CAPEC which is an attack pattern. From the CAPEC, we have the ATT&CK which is the actual procedure of the attack.
This is important because we need to know the vulnerability that exists but it is also good to know how exactly it can be exploited. Especially for newer security analysts that may not know based on the CVE definition how it will affect their attack surface of their organization.
What we built
In our ASM tool, we built something that not only pulls back the CVE’s that exists on a port but we built an attack map that from the results of a vulnerability scan, it will map the port that the vulnerability exist on but will also show the relationship of CVE → CWE → CAPEC → ATT&CK which build an detailed view of what hacker could do to exploit the endpoint. I built an internal database that we called SurfDB, using MySQL, that mapped all of the open source data from MITRE and based on the CVE found it returned all the data related to it in one single query. It was a fun project.
Conclusion
Very important to know this MITRE framework. We thought it would be a very cool feature but ultimately, like other startups, we ran out of funding.
Power to the players, I guess.